Expert Guides to Enhance Cyber Security
Our Featured Articles

Can Avast Detect Keyloggers?
As I notice the work of cybersecurity, I wonder if my trusted Avast antivirus…

What Is Brick VPN?
Finding Brick VPN was a total win. It’s super easy to use, stands out…
[SUGGESTED]How to Make an INI File?
INI files, short for Initialization files, are commonly used to…
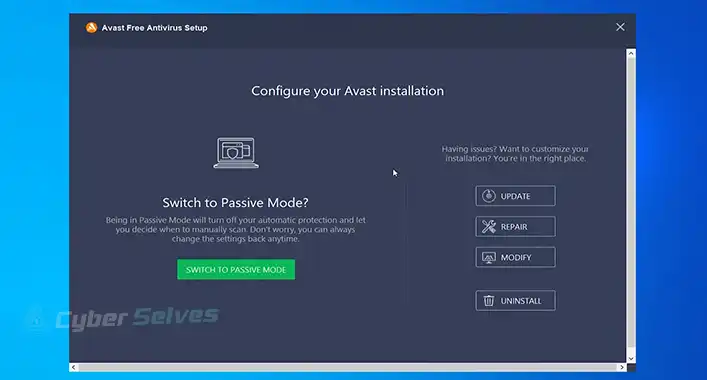
Can’t End Avast Process
Ever found yourself in the digital labyrinth where you desperately…
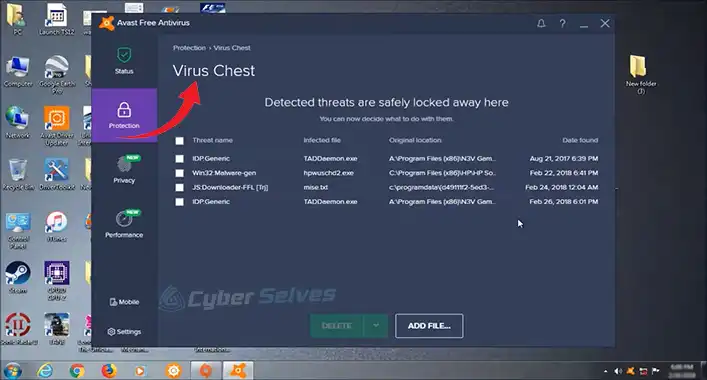
How to Remove File from Avast Chest
Ever faced trouble removing files from Avast Chest? Well, I…
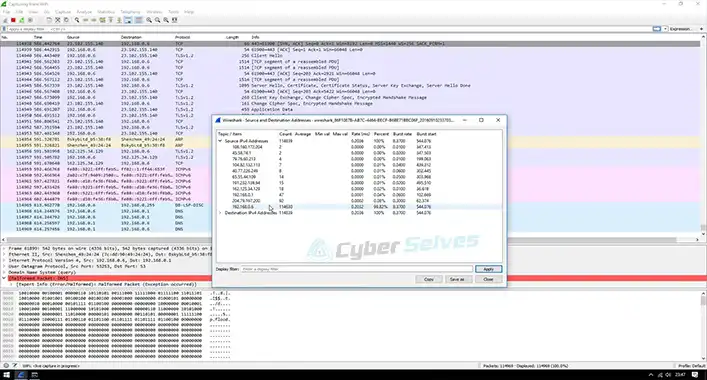
How to Report a DDoSer | Safeguarding the Digital Realm
The modern era of connectivity has ushered in countless conveniences,…
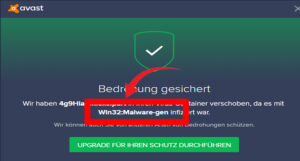
What is Win32 Malware-gen Avast? Protection and Removal Guide 2023
The risks of generic threats are getting more common day by day. These generic threats are…
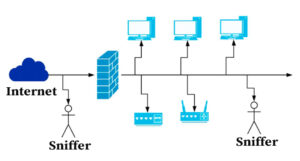
How to Prevent Packet Sniffing Attack | Reasons and Prevention Process
As days go by, the world of information and technology is expanding. The security system and…
Vavada Casino – безопасная платформа с бонусами, поддержкой и лицензией
Официальный сайт Vavada предлагает современный подход к онлайн-гемблингу: здесь доступен обширный выбор ставок, щедрые бонусы и круглосуточная техподдержка. Казино выделяется удобным интерфейсом и мобильными приложениями, позволяющими играть с любого устройства. Репутация бренда подкреплена положительными отзывами, стабильной работой и высокими стандартами безопасности.
Для обхода возможных ограничений используется рабочее зеркало Vavada, полностью повторяющее оригинальный сайт. Оно защищает личные данные и поддерживает доступ к играм даже при блокировке основного ресурса. Зеркало удобно как для пользователей ПК, так и для владельцев смартфонов. Новые ссылки публикуются на официальном сайте и предоставляются службой поддержки.
Регистрация на платформе Vavada проходит быстро: достаточно заполнить форму, подтвердить e-mail и авторизоваться. После входа игрок получает доступ ко всем возможностям сайта. Однако при вводе личных данных важно избегать ошибок, поскольку от этого зависит вывод средств. Проверка личности и соблюдение условий являются обязательными этапами.
Служба поддержки Vavada считается одной из сильных сторон площадки. Пользователи могут рассчитывать на:
- круглосуточный онлайн-чат;
- поддержку по e-mail;
- быстрое реагирование на запросы;
- помощь даже до создания аккаунта;
- компетентность консультантов.
Это делает процесс взаимодействия с казино комфортным и прозрачным, даже в случае технических сложностей.
Вавада официальный сайт казино действует по лицензии Кюрасао, что гарантирует легальность и честность операций. Казино придерживается принципов ответственной игры и обеспечивает высокий уровень защиты данных. Благодаря этому пользователи могут не сомневаться в надёжности платформы и безопасно вносить депозиты, не опасаясь за конфиденциальность или игровую справедливость.
Рабочее зеркало и функциональные возможности сайта Vavada
Чтобы сохранить стабильный доступ к казино Vavada при блокировках, используется рабочее зеркало – копия официального сайта с другим доменным именем. Оно позволяет входить под существующими данными, делать ставки и пользоваться полным функционалом. При необходимости можно получить новое зеркало через поддержку. Дополнительно доступны альтернативные способы обхода ограничений, включая VPN, анонимные браузеры, приложение и e-mail-рассылку с актуальными адресами.
Вход на сайт Vavada возможен с любого устройства – от ПК до смартфона. Интерфейс платформы простой и удобный, каталог игр включает автоматы, покер, бинго, карточные игры. Проблемы со входом решаются службой поддержки. Личный кабинет открывает доступ к управлению профилем, а все действия защищены SSL-шифрованием, что обеспечивает полную безопасность транзакций и конфиденциальность данных.
Среди поощрений для новых и активных игроков:
- 200 € без депозита и 100 фриспинов за регистрацию;
- 100% на первые три депозита;
- ежемесячный кэшбэк до 1000 €;
- бонусы по промокодам 2023 и 2024 годов;
- активные вращения сроком действия 7 дней.
Регистрация на vavada проходит быстро и доступна через банковский счёт или классическую форму. После создания аккаунта открывается доступ ко всем играм и акциям. Регистрация доступна пользователям старше 18 лет. Интерфейс сайта позволяет удобно управлять данными и балансом, а участие в играх возможно с любых устройств.
Ставки на спорт в Vavada охватывают футбол, теннис, киберспорт и другие дисциплины. Навигация по видам спорта интуитивна, доступны прямые трансляции событий. Благодаря фильтрам, поиску и удобному интерфейсу, ставки делаются легко и быстро. В разделе представлены как предстоящие матчи, так и популярные экспрессы, что делает платформу удобной для ставок с любого устройства.
Kasyno bez weryfikacji 888Starz Do grania: Szalone Zakłady, Błyskotliwe Wygrane i Niekończąca Się Przygoda w Świecie Hazardu!
Kasyno online Blackjack 888Starz Licencja jest jednym z najbardziej popularnych miejsc, gdzie miłośnicy hazardu mogą znaleźć doskonałą rozrywkę. To miejsce, w którym liczba gier do wyboru przekracza 2000, co sprawia, że nawet najbardziej wymagający gracze znajdą coś dla siebie. Oprócz klasycznych gier takich jak ruletka, blackjack czy automat do gry, Kasyno oferuje także unikalne opcje, takie jak wirtualne sporty czy e-sport. Wysokie bonusy powitalne, turnieje z dużymi nagrodami oraz niezawodne metody płatności sprawiają, że każdy gracz może poczuć się wyjątkowo podczas gry.
Co wyróżnia Kasyno Darmowe spiny 888Starz Weryfikacja konta spośród innych platform hazardowych, to innowacyjny system lojalnościowy, który nagradza graczy za ich aktywność. Za każdą postawioną złotówkę gracz otrzymuje punkty lojalnościowe, które można wymienić na ekscytujące nagrody, bonusy czy dodatkowe obroty w grach. Ponadto, Kasyno oferuje możliwość obstawiania na sporty wirtualne, co dodaje dodatkowego elementu emocji i rywalizacji. Dzięki nowoczesnej platformie mobilnej, logowanie do konta gracza w jest szybkie i wygodne, pozwalając graczom cieszyć się rozrywką w dowolnym miejscu i czasie.
Jeśli jesteś fanem gier hazardowych, Kasyno Kod promocyjny 888Starz Wypłacalne to miejsce, do którego warto się wybrać. Możliwość gry z prawdziwymi krupierami w sekcji kasyna na żywo sprawia, że doświadczenia z gry są bardziej autentyczne i ekscytujące. Oprócz tego, liczne promocje i turnieje tematyczne pozwalają na zdobycie dodatkowych nagród i przeżycie niezapomnianych chwil. Wystarczy jedno Logowanie do konta gracza w 888starz, by otworzyły się drzwi do fascynującego świata odmian hazardowych i niekończącej się przygody. Dołącz do społeczności Kasyna Mobilne 888Starz Live chat już dziś i ciesz się niezapomnianymi emocjami oraz szansą na spektakularne wygrane!