How Can an Attacker Execute Malware Through a Script? How Is It?
Malware is a program that is designed specially to damage a computer device or system. It is injected into a device or system to cause different types of damage. A hacker or cybercriminal can completely exploit a system by injecting malware into the system. They use different techniques to inject malicious code into the system. Executing malware through a script is a new technique of a malware attack. In this technique, the hacker uses different types of programming languages, including JavaScript and PHP. This programming language is used to create malicious scripts and then deliver the script to the targeted device.
What is Script-Based Malware?
As you know, there are many types of malware that are injected into a system to cause overall damage to the system. Script-based malware is a kind of malware that leverages existing applications and tools of a device or system. It is smart enough to play false the security solutions of the system. Hackers or cybercriminals can apply this sophisticated technology to capture login credentials, compromise data, and cause overall damage to a system is the only drawback of this type of malware attack is that it requires user interaction. So how it exactly works?
What are the Functions of Script-based Malware?
Programming or coding language-based scripts are the main function of this type of malware attack. The hacker or cybercriminals creates a malicious script by using the programming or coding language or programs. Python, Java, PHP, SQL, and C programming, are the programming languages that are mostly used to create these malicious scripts. These programming languages are mainly used by programmers to create a program or software. And you know, some programs or software are malicious for the system. Script-based malware is one of the malicious programs that create the exploitation of a system or device.
The script-based malware poses many advantages to the attacker; they are pretty much easy to create and execute, able to play false the system security system, polymorphic, and extremely effective. The attacker uses various types of scripts to execute this type of attack. Scripts like PowerShell, VBA (Visual Basic for Applications), VBS (Virtualization-based Security), HTML (HyperText Markup Language), JavaScript, and batch scripts are most commonly used by attackers to execute script-based malware attacks.
JavaScript codes can be applied by the cyber attackers to persuade the target for visiting an infected or malicious domain. This helps the cyber attackers or hackers to take control over the targeted system after turning the target into a victim. While HTML-based malware is directly delivered to the targeted device.
How Can an Attacker Execute Malware Through a Script?
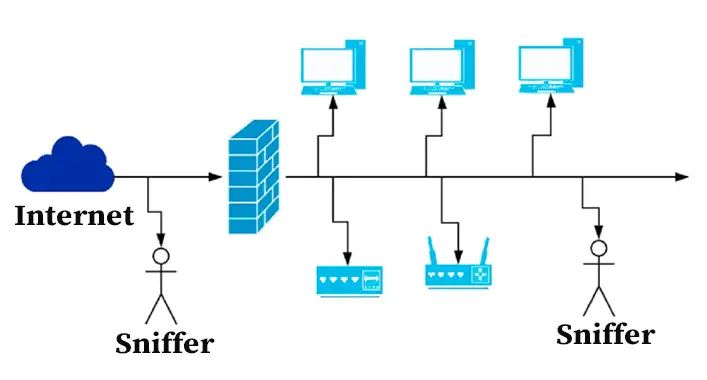
The script-based malware attacks are implemented on a system by using a malicious script. These malicious scripts can be delivered to the targeted device by using many techniques. Attackers make the target download the program through email, text messages, or PDF files that contain malicious scripts. In other techniques, the attacker uses JavaScript or HTML programs to execute the malware script on the targeted device. The HTML programs mainly deliver on the targeted device as an attachment or extension. The one and only drawback of executing malware through script are, it requires user privileges on the system to run and give away the control to the attackers. While using JavaScript-based malware scripts are typically executed on the targeted device by luring the targeted device to visit a malicious or infected domain. This allows the attackers or hackers to take full advantage of system vulnerabilities while taking full control over the device system.
After taking full control over the targeted device system through the malicious scripts, the attacker plays false the security system of a device system by using legit components like PowerShell of Windows operating system. PowerShell allows the user to speed up and spread the infection over the entire operating system. After entering and taking full control, the malware allows the user to execute the motive of the attack. These motives could be data encryption, stealing personal and sensitive data, capturing login credentials, or other destructive operation of the victim device and its user.
How to Remove/Detach Script-based Malware from a Device?
Unusual activities on the device system are noticeable on an infected device. You may notice an installed unknown application, running PowerShell always in the background, strange domain address on the browser history, and other unusual activities when your device is infected by script-based malware. To detach script-based malware from an infected device system, you can follow these below-described tips;
1. Completely deleted all the recently transferred or downloaded files and all types of email attachments including Word and PDF files from the device. These files could be the main resource for executing the script-based malware on the device.
2. Uninstall or remove all types of anonymous applications and programs from the device system. It is highly possible for them to install after the malware execution.
3. Check for harmful and suspicious file scanners if you are using the Google Chrome browser. It has a built-in malware scanner that is capable of detecting script-based malware.
4. To stop the malicious script from running and spreading over the operating system, you need to disable the script on your browser.
5. As you know, PowerShell allows the user to speed up and spread the infection over the entire operating system. So, you need to disable the PowerShell of your Windows device to stop the malware. Also, this will allow the security system to detect malicious scripts.
6. Use a third-party security scanner and perform a full scan of the device after disabling the PowerShell. Now, the security system of the device will be able to detect the malware script while scanning. You know what to do after detecting the script.
7. The attackers could have changed or modified the system settings. So, it is recommended to perform a reset or restart of the device system. You can also perform a system restore from a saved restore point.
How to Protect a Device from Script-based Malware?
Though the detection and detachment process of script-based malware attacks seems to be a complex process, avoiding script-based malware is not that complex. You need to follow some tips to beat up the script-based malware attackers. Here are the tips, that can ensure the protection of your device system as well as you against the attackers;
1. Never ever accept requests from an unknown domain to download any type of file. Unknown domains can use to inject malware into the targeted system. So, always avoid eye-catching pop-ups from unknown or unsecured domains.
2. Avoid emails or text messages from unknown sources. Never download or run any attachments from emails or messages sent from unknown sources.
3. Outdated versions of browsers can be vulnerable to malware attacks. So, always remember to use the updated version of the internet browser. Update it whenever an update is available.
4. Operating system releases update to fix the vulnerabilities of previous versions. Installing the updated version of the operating system can keep cyber attackers away from your device system.
5. Enable WPA or WPA2 protocol on the Wi-Fi network to make it more secure against cyber-attacks.
6. Keep the updated version of the system firewall and third-party security application used on the device system. The updated version of them is more efficient to beat cyber attackers.
7. When surfing through the unknown or unsecured domains, remember to turn off the scripts of your browser.
Frequently Asked Questions (FAQs)
Can a Third-party Security Tool Detect Script-based Malware?
In this type of malware attack, the attacker uses a malicious script to invade a device system. Also, it uses legit components to spread the infection on the entire operating system. For this, script-based malware is hard to detect through the third-party security tool.
Is it Safe to Allow Scripts to Run on an Organization’s Network?
Yes, it is safe to allow scripts to run on an organization’s network, but the system admin needs to control and monitor the network traffic to avoid threats. Also, it is necessary to educate the employees about safe and secure internet browsing.
How Common are Script-based Malware Attacks?
An endpoint security report of 2020 from Ponemon institute addresses that 40% of the cyberattacks are conducted by using some kind of script-based malware. This report shows how common script-based malware attacks
Aftermath
At this point, you have known enough about the script-based malware and its execution process on the targeted device. Beating the script-based malware attacks is not a hard nut to crack, secure and safe browsing of the internet can easily beat up this type of attack. That’s all for today, never forget to securely browse through the internet.