Which Type of Phishing Attack Targets Specific Users?
Phishing can be of all sorts, some easily categorized while others are a bit too far from being mainstream. That said, some phishing attacks which target specific users are spear phishing and whaling.

The former aims towards corporate individuals, asking for favors while pretending to be someone from within their organization. On the other hand, whaling aims straight at CEOs and high-profile persons. Phishers use their identity to access protected info or initiate malicious transactions.
What Are the Types of Phishing Attack
Below are the most common phishing attacks that can possibly come at you or your organization.
Email Phishing
Email phishing is often known as deception phishing. Regardless, it basically uses emails trying to make you click on something, a link or file attached. The messages usually come from malicious sources trying to impersonate a well-known brand.

Generally, links in such emails will land you on malicious web pages and try to steal your credentials. Also, they might even prompt you to install apps portrayed as essential. But in reality, they almost always turn out to be malware.
Email phishing, due to its free and broadly accessible nature, is one of the most popular among attackers. And they are usually sent in bulk. However, that makes it a not-so-popular choice if a cybercriminal were to target a specific user.
That also means identifying such threats is somewhat easier. For example, you should be able to spot illegitimate info about the brand, shortened links, or fake brand logos.
HTTPS Phishing
If a link uses HTTPS (Hypertext Transfer Protocol Secure) instead of HTTP, that proves its legitimacy to some extent. So, most organizations have shifted to using HTTPS. Nevertheless, criminals are also aware of this and have started doing the same.
Therefore, it is better to inspect a link before you click on it. The best practice is to avoid links shortened or embedded as clickable hypertexts.
Spear Phishing
Spear phishing is a form of email phishing without its bulk nature. It is more catered towards criminals interested in targeting individuals. Long story short, Open Source Intelligence (OSINT) is what helps attackers collect data from public sources or social media. That data gets used to narrow down the target domain.
Vishing
Vishing is the short form of Voice Phishing, a term used to describe the situation where a cybercriminal would call a person over the phone. Their primary goal would be to create a false urgency so that the individual gets forced to do as told.
Criminals take advantage of stressful times like the tax-paying season and often act as officials concerned with an audit. So, note the timing of the call and be careful of giving away personal information to avoid being a victim of vishing.
Smishing
It is a form of vishing, which uses text messages instead of voice calls to make the recipient panic and give away data. Such texts, often identifiable through abnormal area codes, may also include suspicious links and files.
Whaling
Whaling, aka CEO fraud, is like spear phishing, except that it targets CEOs and senior members of an organization. So, OSINT comes into play, letting cybercriminals impersonate such members using identical email accounts. They usually request financial transfers or access to confidential documents.
Clone Phishing
Clone phishing takes advantage of widely used services by corporate people. Attackers are aware of business applications where you have to click on links. So, they send emails that pretend to be coming from those applications and services.
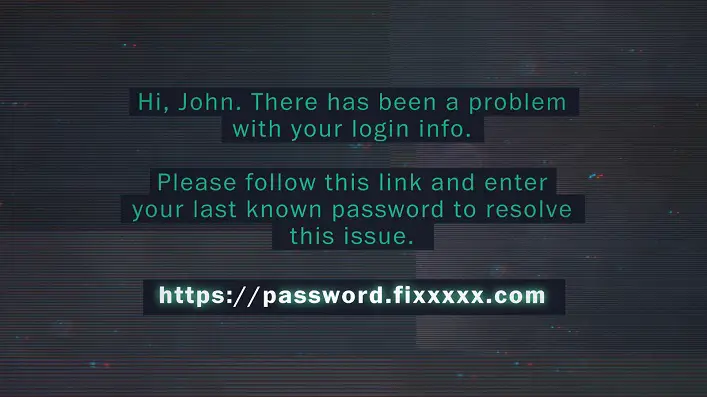
Business applications described above will rarely ask for your personal information through emails. Thus, if you notice such requests, consider it a clone phishing attempt.
Pharming
Unlike most phishing attacks, pharming is typically a hard one to detect, given its technical nature. What happens is attackers hijack the DNS server of a website. After that, whenever a user tries to access the site, he gets redirected to the attacker’s website instead.
Although such websites might have an IP address that looks authentic, mismatched colors or weird-looking fonts will often reveal their fake nature.
Do Phishing Emails Target One Specific User?
Not all of them target specific users, with spear-phishing emails being the exception. These typically contain data targeted towards the recipient only to convince them easily. Attackers collect such info and use them to trick the recipient into taking actions that are usually not in their best interest.
Which Type of Phishing Attack Targets Specific Users – What Is a Targeted Phishing Attack Called?
A targeted phishing attack can be either spear phishing or whaling.
Spear Phishing
As mentioned earlier, spear phishing is one kind of email phishing that targets specific users. The trick here is to collect info through OSINT to impersonate someone and fool other people within the same organization. As a result, the target user believes the email to be a legit internal request, handing over valuable data.
How to Identify Spear Phishing?
A couple of ways to spear phishing identification is as follows-
Unusual Requests
An easier way to detect spear phishing is by looking out for abnormal requests from within the company. For example, someone from another department who shouldn’t have business with you asks for favors out of nowhere.
Shared Folders on Cloud Storage
Spear phishing emails often include links to shared folders across platforms like Google Drive, Dropbox, and Microsoft OneDrive. Avoid clicking on such links right away only because they came from what seems to be a colleague. That is because you may get redirected to malicious websites.
Documents with Passcodes
Password-protected documents are part of a method phishers use to steal credentials. So, be wary of files that ask for a login ID and password.
Which Type of Phishing Attack Is Specifically Directed at Senior Executives or Other High-Profile Targets Within an Organization
Generally, whaling is the type of phishing attack that targets senior executives and other high-profile persons inside a company.
How to Identify Whaling?
You can identify whaling by-
Check Your Email Address
Confidential requests from such high-profile individuals will always come to your work email instead of the personal one. So, if you use an email application for all your work and personal emails, check to which address the request arrived. If it is your personal email account, the email is most likely a fraud.
Abnormal Requests
If the senior executive has never contacted you via email and suddenly comes up with a confidential request, it’s probably spam. So, confirm the request through in-person contact instead of blindly fulfilling the request.
How to Prevent Targeted Phishing?
A few ways to get rid of such phishing include the following.
Deploy Email Filters
Email filters help scan potential phishing attacks and store them in a separate spam folder. Use such a service to filter out spear phishing or clone phishing emails.
Do Not Delay Security Patches
The purpose of security updates is to prevent potential data breaches through existing security holes. So, always try to install these patch updates as soon as they start rolling out.
Use Multi-factor Authentication
Almost all applications and online services nowadays offer at least a two-factor authentication through email or SMS. Make use of this method to keep phishers out of sight.
Final Words
Phishing attacks that target specific users are well-researched attempts, hence harder to detect. Attackers do their homework before impersonating an individual, making it seem as authentic as possible. So, the best prevention method would be to train your employees against potential attacks.