What is Malware-gen Avast? How to Remove it?
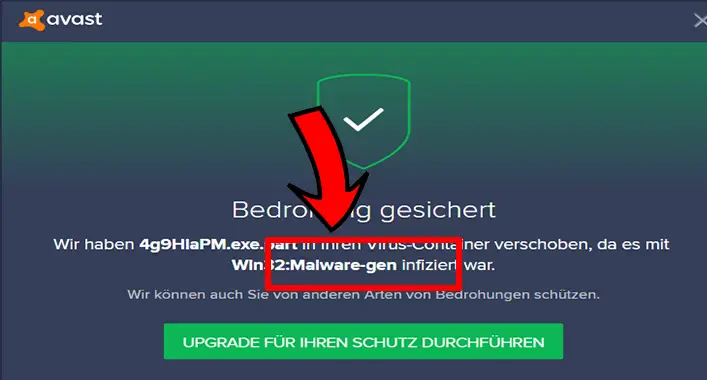
The Malware-gen is a specific detection to detect malicious threats that aim to drop other malicious threats on the infected device. It is a kind of Trojan horse that allows other different malicious programs to get into the infected device. This version of malware is a constant threat to the security of a device. Hackers…