How to Prevent MITM (Man-In-The-Middle) Attack | Detection, Protection, and Impacts
In modern business and organizations, communication is one of the most important parts. Confidential data, information, and files are shared with others to ensure maximum productivity and competitive advantages. Most of the communications are internet-based, which presents an opportunity for cybercriminals to intercept the communication and data transmission system. Man-in-the-middle attacks are such kinds of interception.
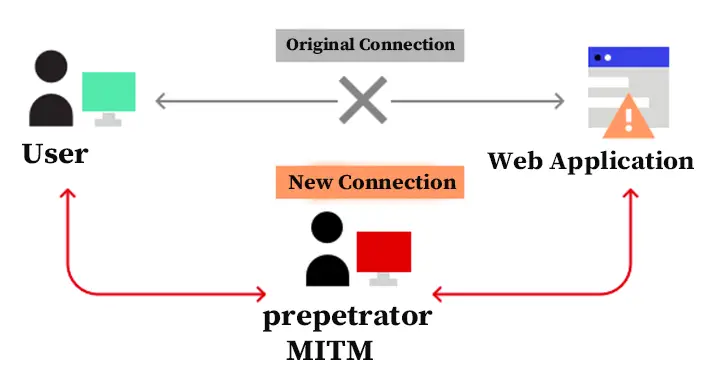
What is a Man-in-the-Middle Attack?
Though the MITM attack is commonly abbreviated as Man in The Middle attack, it is also referred to as Monster in The Middle, Machine in The Middle, Monkey in The Middle, Meddler in The Middle, or Person in The Middle (PITM) attack by the cybersecurity experts. In this type of cyber-attack, the attackers secretly hide on the communication system or a data transmitting system. The attackers can relay or modify the communication between multiple parties who believe that they are communicating with themselves. Also, the attacker is able to intercept all the relevant chats, messages, and texts between the victims and inject new ones into the conversation. On the data transmitting process, the attacker could easily redirect or relay the data transmission process.
What are the Purposes of Man-in-the-Middle Attacks?
Man-in-the-middle attacks could be conducted for many purposes. Commonly, the purpose of conducting this attack is to cause potential damage. Some key purposes of MITM attacks are given below;
- MITM attackers position themselves as proxies on a communication or data transfer system.
- Enable the attackers to stealthily exploit the communication and data transfer system.
- Leaking and stealing confidential data and information and accessing the login credentials regarding trade secrets and financial details.
- Inject malicious codes, programs, and links as legitimate data of the victim.
- Gathering all the collective and achieved data of a communication or data transfer system without user permission.
What Are the Real-World Impacts of a Man-In-The-Middle Attack?
The MITM attackers have increased their reach in cybersecurity landscapes by being a very common cyber threat in recent days. From the cable haunt vulnerability exploitation to snooping on more than half-billion browser users, the man-in-the-middle attacks proved their presence as a very common cyber threat of recent days. Along with the DDoS, Phishing, and SQL attacks, cybercriminals include the man-in-the-middle attack as a primary attack technique to launch significant cyberattacks. So, it needs to be counted as a major threat to the cybersecurity system around the world.
How Many Types of Man-In-The-Middle Attack? / What Are the Techniques/Method of Man-In-The-Middle Attacks?
The types of MITM attacks depend on the method of the attack characteristics. Here are the 6 types of man-in-the-middle attacks;
1. Fake Access Point
Wireless card-equipped devices often try to connect automatically to the wireless access point with high signal strength. The MITM attackers host an access point to trick the nearby devices to join its domain automatically. These access points are named Evil Twin. In this way, the attacker can manipulate all the victim’s network traffic whenever they join the fake access point created by the attacker. This type of MITM attack is the most dangerous because the attacker does not even need to be on a trusted network. Restricting the physical proximity is necessary to perform this type of MITM attack.
2. ARP Spoofing
Address Resolution Protocol (ARP) is used to resolve the MAC addresses (Media Access Control) in a LAN (Local Area Network). Whenever a host contacts another host through the IP address, it references the ARP cache to resolve the IP address into a MAC address. An attacker could act as a host for responding to the requests with his own MAC address. With some precisely placed package, an attacker can easily access the private traffic of two hosts to extract the information from it.
3. DNS Spoofing
Like ARP, DNS is used to resolve the domain names to IP addresses. In this type of MITM attack, the attacker attempts to introduce corrupt DNS cache information to a host for accessing another host by masking the domain name. Which leads the victim to send sensitive information to a malicious domain unknowingly.
4. IP Spoofing
Internet Protocol (IP) is used for routing and addressing data packets to travel across the network system. In IP address spoofing MITM attacks, the attacker creates a false IP address which sources to impersonate other computing systems or networking systems to break down. This method is most commonly used as a primary method of DOS attacks.
5. Cookie Hijacking
Cookie hijacking or session hijacking is a method that is used to exploit an online session to gain access to the information and services provided on the server, device, or website. This type of MITM attacker targets the sessions of browsers and web applications that are often used to pay.
6. Man-in-the-bowser
In this type of MITM attack, the attackers exploit the vulnerabilities of a browser or web application to inject Malicious codes, Malware, Trojans, and other types of programs to capture the private information of a user or organization.
What are the Key Vulnerabilities of a System?
Some key vulnerabilities increase the chance of a system getting attacked by MITM attackers. Below-described things are marked as the key vulnerability of a system;
1. Unsecured Protocols
The unsecured network protocols allow the MITM attackers to enter a system. Whilst the secure protocols keep away the attacker from your system. So, always make sure to use secured network protocols.
2. Spamming
Fake texts, emails, messages are pretty risky. The MITM attackers deliver malicious links through them, which could be mostly malicious. To avoid any types of cyberattacks, it is always helpful to avoid these spam emails.
3. Public Wi-Fi
To be honest, the public Wi-Fi access points can allow access to your system for cybercriminals, including the MITM attackers. It is recommended to avoid public Wi-Fi as much as you can, use a VPN service whenever you use public Wi-Fi.
4. Malware Infections
Most cybercriminals use malware to steal or sniff personal and confidential information. So, you need to be aware of the malware infections of your device and system. To do this, you always need to keep updated versions of the anti-malware applications and firewalls.
5. Non-encrypted Data
Non-encrypted data is easily accessible for an attacker. An attacker could not easily reach and collect information from encrypted data. To avoid information leaking, encryption always helps.
6. Unsafe Browsing
Unsafe and unaware surfing through the network always has a high risk of getting attacked by cybercriminals and hackers. It is recommended to avoid non-secure websites and unusual pop-ups to reduce the risk of hacking and other cyber threats.
How to Detect a Man-in-the-Middle Attack?
Though it is nearly impossible to detect man-in-the-middle attacks, some signs are noticed on the affected device. You can detect a man-in-the-middle attack by reviewing these below –described signs;
1. Fake Websites
While accessing a website, look for HTTPS at the start of the website URL. The secured websites always use HTTPS as the primary protocol. If you redirect to a website whose URL starts with HTTP instead of HTTPS, avoid that website, especially when you are accessing a website following the URL from texts, messages, or emails. Noticing an unusual, even slight variation on the URL address is a sign that addresses your connection was intercepted.
2. Abnormal Pop-ups
Unusual and abnormal pop-ups on the browser screen are another sign of MITM attacks. If you notice an intrusive and sudden pop-up with urgent messages, never click on that pop-up. That could be a gateway to malicious websites. Appearing these pop-ups means you are already on the edge of a MITM attack.
3. Suspicious Certification
Every legitimate and secured website has a legitimacy certificate that is issued by the certification authority, which verifies the ownership of the website. While browsing through a website, if your browser displays a certification warning, that could be a website redirected by the MITM attackers. If you often notice this type of certification warning, it means you are probably a victim of a MITM attack.
4. Disconnections
Repeated and unusual disconnections from the network systems and repeated appearance of the login pages are a sign of MITM attacks. It usually happens when the attacker attempts to access the login credentials of the victim.
5. Unauthorized Activities on the Browser
Unauthorized or unusual activities (strange pop-ups and web addresses, browsing history, cookies) on your internet browser could be a sign of possible MITM attacks. If you notice any changes on the internet browser, which are not made by you, you need to contact an IT specialist or cybersecurity expert as soon as possible.
How to Prevent MITM (Man-in-the-Middle) Attack?
As the old adage Prevention is better than cure, it is better to prevent the MITM attack. As said before, it is nearly impossible to detect man-in-middle-attacks, that’s why preventing it could help you to beat the attackers. Below-described security steps can help you to avoid the potential threat of man-in-the-middle attack;
1. End-to-end Encryption
End-to-end encryption doesn’t allow third parties to reach and read the texts of conversations. It prevents potential eavesdropping and for this reason, it is used in most confidential and secured communications. Encrypted conversation and data packets are pretty tough to decrypt by the third parties, or sometimes it appears to be junk files for the third parties. This means the attacker couldn’t access your files even when you are a victim of MITM attacks. Some social messaging applications offer end-to-end encryption to their users.
2. Using VPN
Virtual Private Network (VPN) encrypts all your data packages whenever they start traveling around the network systems. Also, the VPN connection allows you to establish a secure network connection, even when you are using public Wi-Fi access points. So, VPN connections are essential to establish a secure connection and keep away intruders from accessing your data.
3. Avoid Public Internet Connections
As said before, a fake internet access point could increase the risks of MITM attacks. Hackers or cyber criminals could set up public Wi-Fi connections for their potential and targeted victims. So, you need to avoid the public internet connection as much as possible. It is strictly recommended to use a VPN connection whenever you use a public Wi-Fi network.
4. Secure Browser Plug-ins
The browser plug-ins are used to manage and process the internet content. Unsecured plug-ins are pretty much vulnerable to cyber threats. So, make sure that your browser plugins.
5. Secure the Communication Protocol
You need to use the secured version of communication protocols that are used on the communication system. The TLS and HTTPS protocols offer robust encryption and authentication procedures that make the system most secure.
6. Multifactor Authentication
Typically, the MITM attacks are conducted by spoofing something or another. Multifactor-based authentication like 2FA can be used to create various layers of the stack to ensure that the parties are not communicating with a third party. It is a public key-based authentication that is can authenticate the actual party.
7. Latest Version of Browsers and Security Applications
Outdated browsers and security applications are more vulnerable to potential cyber threats like MITM attacks. So, it is important to ensure that you are using an updated and secured version of browsers and applications to avoid MITM attacks.
8. Verifying the Domain and Browsers
To avoid the MITM attack, a user always needs to verify the domain name and the browsers before visiting a website. This is necessary for ensuring that you are visiting a secured webpage.
9. Secure the Login Credentials
It is always essential to change the default login credentials of the Wi-Fi router, including the Wi-Fi passwords. When an attacker found the login credentials of a router, they could easily change the DNS server to a malicious server or infect your router with malicious codes.
10. Deploy Security Software on the System
In every computer-based system, it is always necessary to deploy security software to keep away the system from potential threats. The most secure system is less vulnerable to threats. To beat the MITM attackers, an efficient security system for the computing system is essential.
11. Monitoring the Network System Traffic
Regular monitoring of the network system is necessary, especially the network systems that are used by a business firm or organization. It is necessary to monitor the usual-unusual and normal-abnormal traffic of the network system.
How to Ensure Protection From Man-In-The-Middle Attacks on a Business?
For ensuring the protection of business firms, securing the network system is always necessary. Allow encryption to all the communication and file transmission procedures to keep away the MITM attackers from your network systems. Whenever you notice any suspicious activities, contact the IT specialist or security experts.
To ensure the maximum protection of your business or organization from the MITM and other cyberattacks, it is always better to hire a cyber-expert or IT specialist. If the in-house team lacks the resources to cope with the implementation of advanced security measures, you need to contact the IT consulting firms to ensure business protection from MITM and other cybersecurity threats.
Frequently Asked Questions (FAQs)
How Often Should I Monitor the Network System Traffic?
It is always better to monitor the system traffic regularly. If you detect slight unusual traffic on the network system, you need to contact IT specialists or cybersecurity experts. Sometimes, slight unusual changes in the network system traffic indicate a greater cyber threat.
Should I Need to Clear all the Caches and Cookies of the Browser?
Yes, you need to clear all the cookies and caches of your browser after completing the internet sessions. They could be the key reason for further issues with your device and system.
Which Protocol Is Used to Secure Communication?
HTTPS protocols are used to secure communication. It is the secured version of Hypertext Transfer Protocol (HTTP).
Final Words
As cybercriminals are inventing new techniques to hack internet-based systems, the users need to use the secured methods of using the system. Never forget to update the security software and devices to avoid potential threats.


![[Answered] Is Valorant Anti-Cheat Client Malware?](https://cyberselves.org/wp-content/uploads/2022/04/Is-Valorant-Anti-Cheat-Client-Malware.jpg)


