How to Prevent Packet Sniffing Attack | Reasons and Prevention Process
As days go by, the world of information and technology is expanding. The security system and applications of tech devices also getting smarter day by day. With this, the hackers also getting smarter, they are discovering new tricky techniques to hack a system, device, or server.
Packet sniffing is one of the latest tricky techniques that could be a constant threat to any device, server, or system. Though packet sniffing can be used for both good and bad purposes, cybercriminals only use it for malicious purposes.
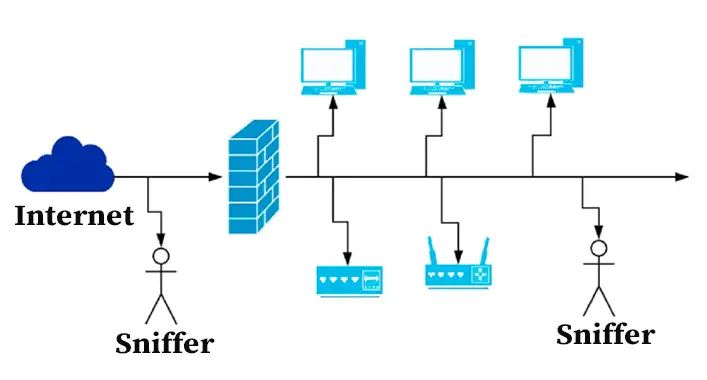
How Does Packet Sniffing Work?
All our data got divided into smaller packets while traveling through the network systems. These packets contain a lot of data about the sender which includes IP addresses, request type, process, and other contents that get delivered to the intended destinations. This allows the receiver party to identify and assemble them in order.
Criminals and intruders can hold and inspect the data packages during their journey to intended destinations. By using the sniffing software, the criminals and intruders convert the data packages into a readable format. This way is nearly similar to wiretapping, where a listening microchip is planted on your telephone or contacting device by the stalkers or agents to listen to the conversations unanimously. The chip planting process is performed in packet sniffing by installing software and inspecting the data before converting the data packages into a readable format. After the conversion process, it is easy to analyze the data piece by piece.
How Do You Prevent Sniffing Attack?
Prevention comes after detection. As we said, detection depends on the sophistication level of packet sniffing. However, if you are not able to detect the sniffing attack, don’t worry, you can still beat it by some methods. These below-described methods could help you to beat sniffing attacks –
1. VPN Service
To beat the sniffing attacks, data encryption is necessary. Data encryption offers the most perfect protection against sniffing attacks. To encrypt your data, VPN (Virtual Private Network) service is necessary. The VPN service encrypts your data and passes it through a secured and encrypted network channel system through the internet. This process makes it tough for anyone to decrypt the intercepted data.
2. Avoiding Public Wi-Fi Connection
While using the public Wi-Fi connection to browse the internet, anyone can sniff your information to facilitate themselves with your data. So, it is better to avoid public Wi-Fi connections. In case, you can use a VPN service while using a public Wi-Fi connection.
3. Using a Secured Protocol
Always use a secured network protocol to avoid packet sniffing. Here, it is recommended to use a VPN service as a confirmation of security. Some extensions or add-ons could help you to increase the security of the internet protocol.
4. Use Sniffer Detection Tools
It is better to use a sniffing detection tool. Using this tool, the server will always look for active and even passive sniffing attacks, detect most attacks, and alert system admins so that they can impede the hacker. Just take the proper time and choose a suitable tool for your business.
5. Upgrade Security Software
An antivirus tool provides you with around-the-clock protection against malware, virus, Trojans, worms, spyware, and other security threats. To knock out the injected virus on the system by the sniffers, you need to use an antivirus tool.
6. Safe Browsing
To avoid packet sniffing attacks, you need to avoid all unencrypted websites. Browsing unencrypted websites increases the risks of packet sniffing attacks. Always remember to avoid spam mails, unusual pop-ups, and never download any content from a non-reputed site.
7. Network Monitoring and Scanning
To protect the commercial network or server system from packet sniffing attacks, it is always better to hire professional network administrators and IT professionals. They will monitor and scan the network and server system. It will keep your system away from packet sniffing attacks and other cyber threats.
Frequently Asked Questions (FAQs)
What is a Wi-Fi Attack?
Cybercriminals and hackers can create fake Wi-Fi to intercept and facilitate themselves with the user data. Wi-Fi attacks are a kind of malicious attack that is performed against wireless networks by tricking the Wi-Fi security to steal the user information (e.g. DDoS, eavesdropping).
Is Packet Sniffing Ethical or Unethical?
Packet sniffing has both ethical and unethical uses. It depends on the purpose of packet sniffing. When it is performed for ethical use (e.g. network diagnosing, surveilling, advertising) it is ethical, and when it is performed for unethical use (e.g. hacking, data leaking, injecting malicious codes) it is unethical.
Can Sniffing Be Used for Complex Hacking?
Yes, packet sniffing could be used for complex hacking. Moreover, through packet sniffing, you can crack down network and server systems. A packet sniffing attack on your network or server system could be a warning for getting affected by complex hacking.
Aftermath
Now, you already know enough about packet sniffing and its usefulness, protection, and detection process. Some security steps can help you to avoid the packet sniffing attack. Always browse safely to avoid cyber issues. That’s all for today, see you again.


![[ANSWERED] Does Malwarebytes Scan All Drives?](https://cyberselves.org/wp-content/uploads/2023/07/Does-Malwarebytes-Scan-All-Drives.webp)


