What Items Are Not Saved During a Configuration Backup and Restore of a Cisco ASA Firewall?
In the ever-evolving realm of cybersecurity, managing a Cisco ASA firewall can be a high-stakes game. You rely on it to protect your digital kingdom, but what if disaster strikes? Enter the hero: configuration backup and restore. However, here’s the plot twist – it’s not a one-size-fits-all solution. There are some items that simply don’t make the cut.
So, what’s the scoop? What exactly doesn’t get saved during a Cisco ASA firewall configuration backup and restore? Buckle up because the essentials like dynamic routing protocols, VPN session info, licensing details, SSL certificates, etc. are left out in the cold.
But you don’t need to worry anymore as we’re here to provide everything you need to know about this matter. Stay with us, and we’ll unveil the secrets of Cisco ASA configuration backup and restore. Armed with this knowledge, you’ll be ready to safeguard your digital fortress and ensure it stands strong against any threat.
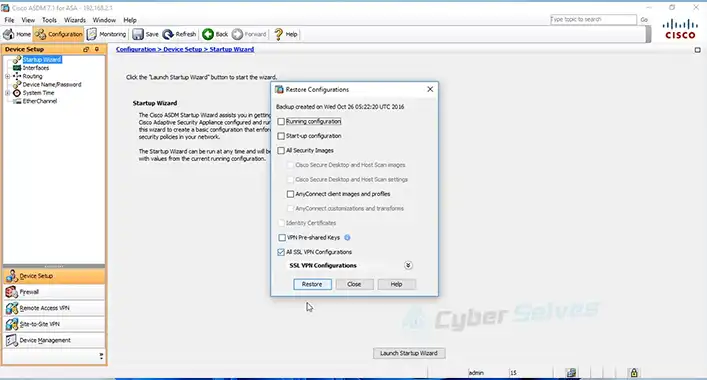
Items That Are Excluded During a Configuration Backup and Restore of a Cisco ASA Firewall
Configuring a Cisco ASA firewall is a meticulous task, involving a multitude of settings and parameters. As network administrators, we breathe a sigh of relief when we perform backups, knowing that our configurations are safe. But here lies the challenge – what if the backup doesn’t cover everything? What if some critical elements are left out?
And unfortunately, some things do get excluded. In a nutshell, during a configuration backup and restore of a Cisco ASA firewall, the following items are not saved:
- 1. Dynamic Routing Protocols
Dynamic routing protocols, such as OSPF and EIGRP, are not part of the backup. These settings must be reconfigured manually post-restore.
- 2. VPN Session Information
VPN session data, including active connections, is not saved. This means that after a restore, VPN users will need to re-establish their connections.
- 3. Licensing Information
Licensing details, like activation keys and expiry dates, are not included. You’ll need to re-enter this information.
- 4. Certificates and Keys
SSL certificates and cryptographic keys are not part of the backup. Make sure to store these separately.
- 5. Captured Packets
Packet capture data is not saved. If you rely on these captures for troubleshooting, make sure to export and save them before the backup.
- 6. Custom Scripts and User Data
Any custom scripts or user-specific data are not covered. Keep separate backups for these items.
- 7. Syslog and SNMP Configuration
Syslog and SNMP settings are not saved during backup and restore. Reconfigure them post-restore to maintain network monitoring.
Now that we’ve highlighted what’s excluded, it’s crucial to prepare for these gaps to ensure a smooth recovery process.
Are Those Items Matter?
Knowing what’s not saved during a backup and restore operation is essential for disaster recovery planning. Neglecting these crucial elements could lead to network downtime and security risks. By understanding these limitations, you can proactively mitigate potential issues and streamline your network management.
Final Thoughts
In closing, while the world of Cisco ASA firewall configuration backup and restore may present challenges, knowledge is your shield. We’ve uncovered what doesn’t make the backup cut, from routing protocols to licensing details. Armed with this insight, you’re better prepared to secure your digital realm. Remember, despite these exclusions, proactive measures can fill the gaps. If you have questions or need clarification, drop a comment below; your engagement fuels our community. Thank you for journeying with us, and best wishes in fortifying your network’s defenses!
FAQs Time
Can I schedule automatic backups for a Cisco ASA firewall?
Yes, you can schedule automatic backups using tools like Cisco Configuration Professional or Cisco Security Manager. These tools allow you to set up recurring backup tasks for your Cisco ASA firewall configurations.
Is it possible to back up VPN configurations separately?
Yes, you can back up VPN configurations separately from the firewall’s main configuration. This is especially useful if you frequently update VPN settings and want to ensure their safekeeping.
What’s the recommended frequency for performing backups?
It’s advisable to perform regular backups, depending on your network’s complexity and rate of configuration changes. For many organizations, a weekly or bi-weekly backup schedule is sufficient, but more frequent backups may be necessary in dynamic environments.
Are there any third-party tools for Cisco ASA backup and restore?
Yes, several third-party tools specialize in Cisco ASA backup and restore operations. Some popular options include SolarWinds NCM, ManageEngine Firewall Analyzer, and TFTP servers like SolarWinds TFTP Server.
Can I automate the restoration process after a configuration failure?
Yes, you can automate the restoration process by scripting it using tools like Python or by using configuration management software. Automation can significantly reduce downtime during recovery efforts.