Expert Guides to Enhance Cyber Security
Our Featured Articles

Can Avast Detect Keyloggers?
As I notice the work of cybersecurity, I wonder if my trusted Avast antivirus…

What Is Brick VPN?
Finding Brick VPN was a total win. It’s super easy to use, stands out…
[SUGGESTED]How to Make an INI File?
INI files, short for Initialization files, are commonly used to…
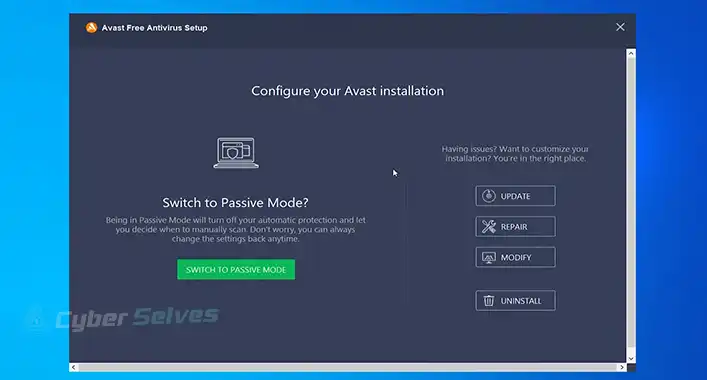
Can’t End Avast Process
Ever found yourself in the digital labyrinth where you desperately…
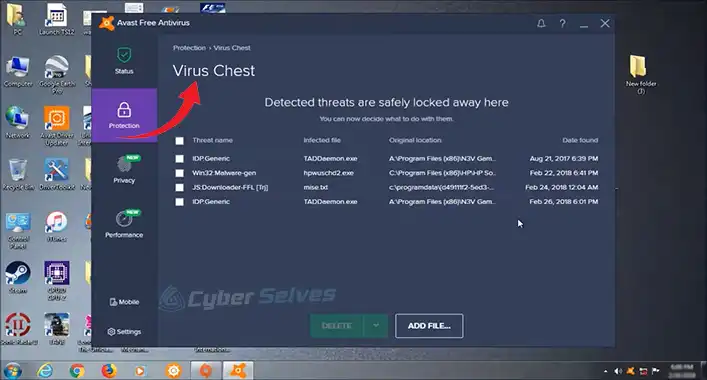
How to Remove File from Avast Chest
Ever faced trouble removing files from Avast Chest? Well, I…
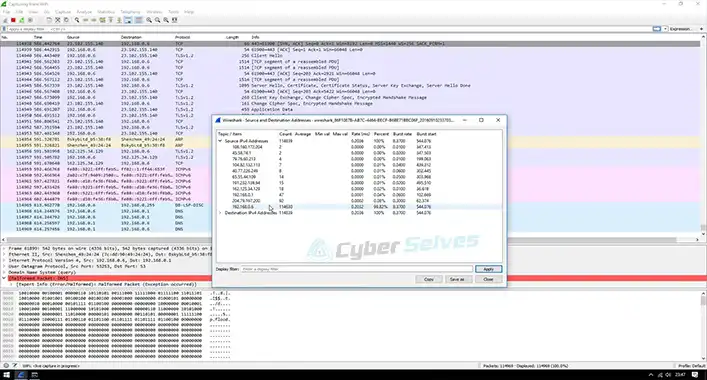
How to Report a DDoSer | Safeguarding the Digital Realm
The modern era of connectivity has ushered in countless conveniences,…
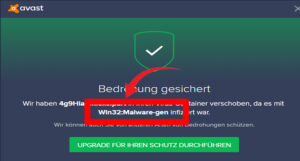
What is Win32 Malware-gen Avast? Protection and Removal Guide 2023
The risks of generic threats are getting more common day by day. These generic threats are…
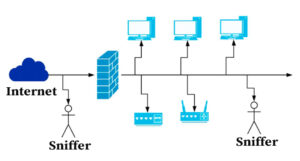
How to Prevent Packet Sniffing Attack | Reasons and Prevention Process
As days go by, the world of information and technology is expanding. The security system and…