What Is TR/Trash.gen? How to Remove TR/Trash.gen?
TR/Trash.gen is the newest version of the virus that is too much harmful to the infected device. The third-party application can only detect it, but they are not being able to take significant action to remove TR/Trash.gen. These antivirus applications make things worse, by appearing pop-ups that say removing of threat has failed and the application won’t let you ignore that application. So, what is this notorious virus? How to get rid of it?
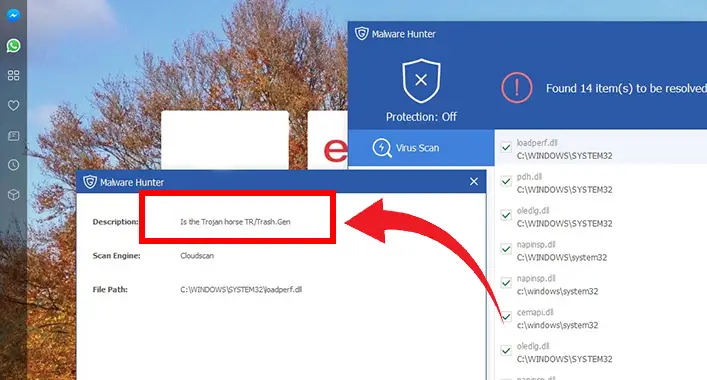
What is TR/Trash.gen in Computer Systems?
The TR/Trash.gen is a type of virus that is able to create multiple issues on an infected device. It is mostly used by online scammers for conducting different types of malicious actions on computer device. This notorious program can affect any type of computer operating system and hugely damage the device system (software, settings, and programs).
Is TR/Trash.gen Is a Trojan Virus?
Trojan horse virus is able to mask up and hide with the system files to not get detected. The TR/Trash.gen also masks up with the system files like the Trojan horse virus. It can also download additional malware on a device and are capable to bypass the system security setting like the Trojan virus. So, the TR/Trash.gen is categorized as a type of Trojan horse virus.
How Could a Device Be Infected by TR/Trash.gen?
A device could be infected by TR/Trash.gen in many ways, mostly by utilizing the system security holes. Even a slight security hole is enough for it to infect a device. TR/Trash.gen can be downloaded and installed on a device system as a dropped file through other malware or an unknown download from a malicious website. Also, a device can be infected by it after clicking on malicious code, unsafe adware, pornographic and gambling websites, and spam emails. In short, careless surfing through the internet without any protection can infect a device with TR/Trash.gen.
What Can TR/Trash.gen Do?
After infecting a device, it opens a backdoor to allow entrance for other malicious applications or programs. Once installed, it can also create some malicious codes and files to modify the device settings and registry entries. Also, it can install additional spyware that includes adware, ransomware, and worms on the device. Through network exploits, it can drop other malicious files/programs/codes that are too much harm to your computer device. This Trojan has the ability to reduce the device performance and change the device setting without any permission. CPU usage could significantly rise high at any time, even when you don’t have any application or website opened in the background. Sometimes, the TR/Trash.gen takes up high resources and slows down device speed as well as the performance of the device, which may cause the device stuck frequently.
TR/Trash.gen can generate disturbing adware pop-up alerts on the device screen to interrupt your online activities. It could stop a user to access some applications by corrupting the application database. Changing the internet browser setting without user permission could redirect the internet browser toward malicious websites and download malicious files, codes, and programs.
A hacker or online intruder can easily access and control a device through the TR/Trash.gen. After messing up the device system through TR/Trash.gen, a hacker could steal/collect personal information from the device. This virus could infect all the programs and files of a device and keep them out of the control of the user in order to give access to cybercriminals and hackers.
Is TR/Trash.gen Detectable?
The TR/Trash.gen is detectable, which masks itself as system files like a Trojan horse virus. This is one of the newest versions of the TDSS Trojan horse virus that was first detected on AVG Antivirus. Though this notorious virus is detectable by third-party antivirus applications, the third-party applications are not able to remove this virus permanently. So, for combating the TR/Trash.gen virus, a manual approach is required. Some methods are highly efficient to remove and reduce the damage caused by the TR/Trash.gen. As said before, the TR/Trash.gen masks up with the system files and contains a random name to mask up, which makes it nearly impossible to detect manually.
Frequently Asked Questions (FAQs)
How Many Antivirus Should I Use on a Computer Running with Windows Operating System?
Windows do not support multiple third-party application on the same device. Performance issues, fighting over files and monitoring processes, accusing one another could be caused if there are multiple third-party applications. So, it is better to keep only one third-party application on the Windows-operated computer device.
What if I Do Not Remove the TR/Trash.gen Virus?
If you do not remove the TR/Trash.gen virus from your device, it could damage the system of the device as well as the performance of the infected device. Also, this virus is a constant threat to the personal and confidential information stored in a device.
Why I Can’t Use a Third-Party Antivirus Application to Remove the TR/Trash.gen Virus?
The third-party application only can detect the virus, but they cannot remove the TR/Trash.gen virus. That’s why you need to follow the manual ways to remove the virus.
Finishing Up
Now, here you are, hope that you have known enough to keep your device safe and secure from the TR/Trash.gen virus. To keep your device safe from cyber threat and all types of malicious applications. That’s all for today, stay safe.


![[Explained] Is Cheat Engine a Malware? How Is It?](https://cyberselves.org/wp-content/uploads/2022/03/is-cheat-engine-malware.jpg)
