Java Malware-Gen [Trj] | Protection and Removal Guide
Cyber attackers invent and use new attacking techniques daily to invade a system. Most of the time they use some types of malicious files, scripts, or viruses to get into and control a system.
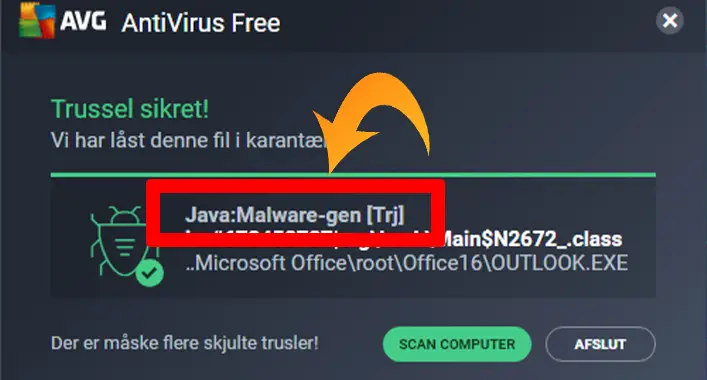
These malicious threats work as a gateway or carrier for other threats on the device system. They are able to cause several types of damage to the device system. Java:malware-gen [Trj] is one of them.
In this post, we’ll find out about Java:malware-gen [Trj], its negative impact, protection, and removal tips. So, let’s get started.
Java Malware-Gen [Trj] – What Is It?
Java:malware-gen [Trj] is a very recent type of highly dangerous ransomware. It is a form of malware that is injected into the targeted device. Also, this can cause damage to the device and the user in many ways. As you know, the attackers can block access to a computer system by encrypting all the files of the system and demanding for paying ransom for the decryption key.
Java:malware-gen [Trj] is a kind of ransomware and generic threat, that could be used for blocking the access of a system to excerpt the ransom from the victim. Also, an attacker can cause a good deal of damage including data leaking, capturing the login credentials, and physical damage to the device. So, how does it work?
How Does Java:Malware-Gen [Trj] Work?
Like other malicious attacks, attackers are required to inject Java:malware-gen [Trj] on the targeted device to turn it into the victim. The attackers can use different mediums as a carrier of this ransomware. Here are the most used mediums used by the attackers to inject it;
- As an attachment with the phishing emails.
- Through an unsecured domain or source that is pretending to be trustworthy.
After a successful injection of Java:malware-gen [Trj] on the targeted device, it starts to cipher the data and information of the victim device. Also, this ransomware is able to interrupt gadgets from working properly. After successfully encrypting the files or blocking access to the system, the attackers leave a ransom note that contains the requirements to decrypt the file or unblock the system access. In most cases, the attacker demands payment to decrypt the file or remove the block from the system functions. The victim finds the ransom note after restarting the infected device.
Nowadays, the circulation of Java:malware-gen [Trj] ransomware is expanding by leaps and bounds around the world. The attacking techniques and the ransom quantity differ. Also, obtaining the process of the ransom may vary depending on the regional settings and payment method.
For example, Java:malware-gen [Trj] may wrongfully identify and report the user about the unlicensed applications or programs on the system and ask for some sort of payment to relieve the user from these applications or programs. In another way, the attacker uses some falsely asserted pop-up that addresses the user about some kind of danger. The attacker asks for a payment to relieve the user from the falsely asserted pop-ups.
What Are the Negative Impacts of Java:Malware-Gen [Trj] on a Device?
Malicious programs are always used to cause some sort of damage to a device system as well as the user. The Java:malware-gen [Trj] is not an exception to that. It may cause a good deal of damage to a device. As said before, it is a kind of Trojan malware that allows the attacker to take control of the device system.
The attacker encrypts data or blocks the access to ask for a payment from the user. In some cases, the attacker stole the data and login credentials from the victim’s device despite paying the ransom. It is possible for the attacker to cause a magnificent loss of the victim. So, whenever you detect Java:malware-gen [Trj] on your device, start removing the process before it gets too late.
How to Remove Java:Malware-Gen [Trj] From a Device?
As you already have known, the Java:malware-gen [Trj] is a threat that can crypt, capture, and leak your data for ransom. Also, it can block access to your device. For these reasons, this Trojan ransomware is a massive threat to your device, and you need to remove it as soon as possible after getting detected.
Removing it from your device is not a hard nut to crack. A complete scan with a third-party anti-malware utility can help you to remove detect and remove it from your device. Just make sure to use an advanced leveled third-party anti-malware utility to detect and remove this generic threat from your device. Also, it is recommended to start the security scan, booting the device on safe mode.
Another way to remove this threat from your device is to restore the device from a restore point. It takes your device to a previous state of your device. In most devices with the Windows operating systems, the restore point is automatically created after an update of OS or installation of a program.
What Can Protect a Device From Java: Malware-Gen [Trj]?
To protect your device from this type of notorious generic threat, you need to follow some tips when using your device. These tips will help you to avoid most of the cyber threats, including Java:malware-gen [Trj]. Here are the tips you should follow;
1. Safe Browsing
You need to be aware while surfing through the internet with your device. Reckless browsing increases the probability of getting infected by cyber threats. Always surf through the secure domain or websites and check the domain address before visiting them. Also, you need to use a secure browser like Google Chrome for secure browsing. Sometimes, browser extensions or add-ons can be a threat to your device. So, you need to be careful while using browser extensions or add-ons.
2. Avoid Spam or Phishing Mails
To deliver malicious attachments on your device, the attacker can use spam or phishing mail. These emails may contain eye-catching and attractive advertisements, offers, or tips. So, avoid phishing and spam mail as much as possible. It is recommended to be careful while opening the domain address or attachment provided on spam or phishing emails.
3. Trusted Source of File Transfer
Nearly in every case, cyber attackers use a medium to inject malicious programs on a device. Using a trusted source for transferring files will help you to protect your device from most cyber threats. Never use any unrecognized or unsecured medium for transferring the file. Also, you need to be careful while downloading something from a domain or website.
4. Use Updated Security System Utilities
The security system of a device is committed to protecting a device from any kind of threat of the device. As you know, the security system is a combination of security utilities that includes a firewall, firmware, and third-third party security tools. An outdated version of security utility is not able to give your device maximum protection against device threats. So, it is necessary to use the most updated version of security tools to get maximum protection.
Frequently Asked Questions (FAQs)
Can Java:malware-gen [Trj] Carry out Dangerous Actions on Infected Device?
Yes, it can carry out dangerous actions on an infected device. Moreover, the attackers can leave other types of malware on the device even after paying the ransom money.
Are Malware-gen Safe?
No, it is not safe for a device. Because the Malware-gen is a kind of potentially unwanted program, it can contain malicious threats which can devastatingly harm a device.
What is a Generic Threat of a Computer?
The generic threat refers to these threats or programs that have features or behaviors nearly similar to a virus. These are PUPs and may contain harmful or malicious programs.
Final Words
At this point, you have known about the removal and protection guide of the Java:malware-gen [Trj]. I hope, this guide will help you to protect your device from further infection of this type of ransomware. Remember to use trustworthy mediums or sources while transferring data. That’s all for today, stay protected, stay happy.


![[Answered] Can a 3DS Get a Virus?](https://cyberselves.org/wp-content/uploads/2023/09/Can-a-3DS-Get-a-Virus.webp)