What Is Sync-eu.exe.bid? Symptoms, Infection, and Removal Methods
There has been a recent increase in reports of trouble with Sync-eu.exe.bid URL from windows users. What’s intriguing about these occurrences is that the affected users certainly will not be able to report anything suspicious because their security software is preventing them from visiting the malicious domain. The most obvious sign of a malware issue is the frequent notifications that follow instances of anti-malware software like Malwarebytes blocks malicious outbound traffic. At first glance, these users may be safe, provided that their security protocols keep them from accessing the malicious site. But on the other hand, it’s alarming that malicious software is actively executing on the device’s internal systems.
What Does Sync-eu.exe.bid Virus Mean
This is a program that may be run by simply opening the file with the “.exe” extension. However, that does not represent the entire fact in any way. The device’s default browser is forced to continuously load the infected URL because the user’s computer is infected with a hidden virus. As it may infect many browsers, the virus provides the same threat to users of all major web browsers, including Chrome, Firefox, and Internet Explorer.
It does not matter how many times the browser tries to correct the entire phrase, sync-eu.exe.bid/bidswitch/sync?sub1=switchconcepts, it always fails. This particular adware program can be recognized by the phrase that is appended to the primary address.
Symptoms of the Sync-eu.exe.bid Virus
There is almost no doubt that sync-eu.exe.bid virus carries significant risks to a network’s security. They can enter your device with the support of a multitude of sources. The following is a list of the methods that cybercriminals employ the majority of the time to transfer malware:
- Requests for updates that could be malicious but appear to be quite similar to the ones that your operating system sends. However, these bogus updates could lead you to websites that contain malware, and if you visit those websites, your computer might be automatically infected with several infections.
- Pop-ups and perhaps other types of ads could be malicious and could redirect users to websites that contain malware.
- Avoid strange texts within your emails or their attachments. If you get any such suspicious letter, you should ignore it and remove it. You have to avoid such attachments as well and stay away from them because they might also spread the infection.
- In this case, the Trojan that is hidden inside of them might also be followed by malware that is similar to ransomware. Ransomware is significantly more harmful. They will prevent access to many of your files, and there are no guarantees that you will be able to unlock such files. In addition, this kind of malware will ask for money from you, but it will never guarantee that it can unlock the data it has locked. Malware combinations like this are probably the most dangerous form of online danger that you may face.
- Other possible causes of Trojans include file-sharing networks like BitTorrent, websites that have been compromised, and unlawful software.
What Can an Infection with Sync-eu.exe.bid Lead to?
The possible issues that could arise as a result of an infection with the Sync-eu.exe.bid may appear on a variety of types. Their total number has also never been specified or confirmed in any way. Neither has been reported. Hackers and other online criminals write viruses to fulfill a large range of purposes each day. The following is a list that are the most prevalent uses for this program:
1. Data Can Be Corrupted or Lost
It’s possible that malicious software called Trojan horses was to blame for the loss of important files. Cybercriminals are the ones that create and disseminate malware like this, and in some situations, they can use it to either completely delete all of the files on your home pc or merely modify this in some way. The impact on both your computer and yourself can be so severe that it may be necessary to do a complete reinstallation of the operating system.
2. Get Your Passwords
Cybercriminals can follow you because they want to spy on you. In addition to this, they may be targeting your passwords for your bank account because they may have the purpose of discharging it. The hackers may have their current focus on the accounts you use for social networking.
3. Hack the Entire Network
Trojan horses collect some professional information that you may own or have full rights to. If your device is connected to the network at your work location, then as soon as a Trojan infects your pc, the entire network will be at risk of being hacked.
4. Get the Device’s Resources
It’s possible that cybercriminals just require access to your computer’s resources. Hackers like this frequently transform random devices into bots to abuse their resources for a variety of unethical operations.
Methods of Sync-eu.exe.bid Malware Removal
There are some methods that you can follow to remove this virus to protect your system and files from any kind of corruption. The methods are the following:
Method 1: Uninstall the Program
Step 1: First, open the control panel. To open the Control Panel, press the Win+R simultaneously from your keyboard, then type control panel into the search box and press enter.
Step 2: Then, from Programs, select the Uninstall a program option.
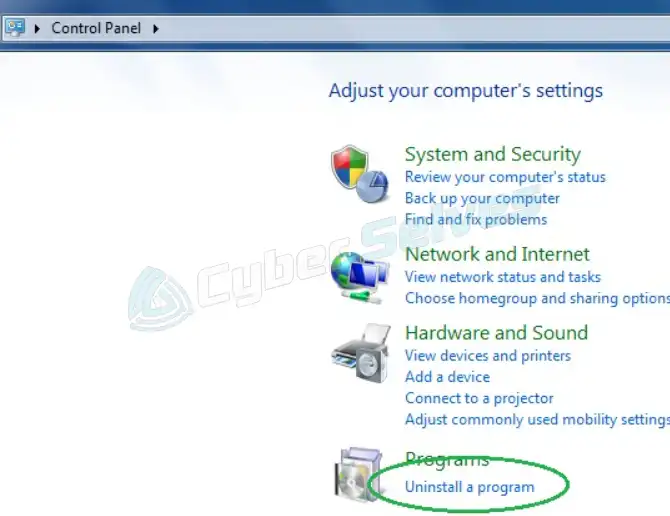
Step 3: Finally, find the software that you do not want, pick it, and after that, hit on the Uninstall button. If you cannot find Sync-eu.exe.bid, look for any unfamiliar apps which you do not recall downloading on your computer. The malicious software may have renamed itself.
Method 2: Remove the Shady Processes
Step 1: First, navigate to the Start menu on your computer, enter Task Manager into the search window, and then open the View running processes with Task Manager option from the list of results.
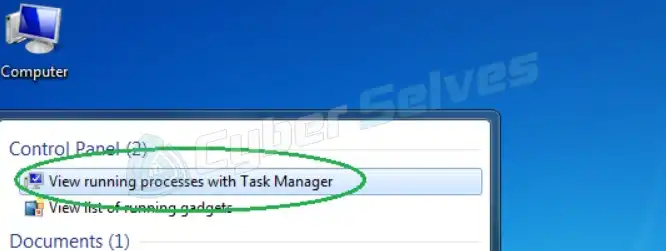
Step 2: Then, examine each and every procedure in full detail. Even though the file Sync-eu.exe.bid may not be around, you should be suspicious of any application that seems fishy and uses a lot of memory because it’s possible that it’s being driven by unauthorized software.
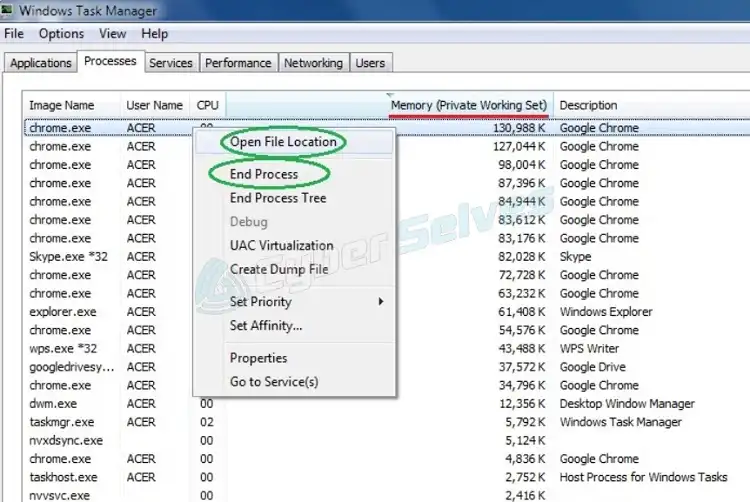
Step 3: If you find the process that’s being run by Sync-eu.exe.bid, you have to right-click on it, open the folder where its files are stored, and remove everything in that folder. Now, return to the Task Manager and terminate the process there.
Method 3: Automated Removal of Sync-eu.exe.bid Virus
The suggested software has a modern database containing malware characteristics and uses smart behavioral analysis to quickly discover the virus, eliminate it, and restore all negative changes. For this, proceed as follows:
Step 1: Get the anti-malware program, and then install it. Launch the solution then click the option labeled “Start Computer Scan” to have it search your system for potentially unwanted programs as well as other forms of dangerous software.
Step 2: Now, the scan report will detail anything that could be harmful to your windows os. To have the repair process completed, you need to select the problematic entries and then select the Fix Threats button.
Method 4: Delete Sync-eu.exe.bid Virus Via the Control Panel
Step 1: In Windows, navigate to the Control Panel by clicking the Start button, and then select the Uninstall a program option.
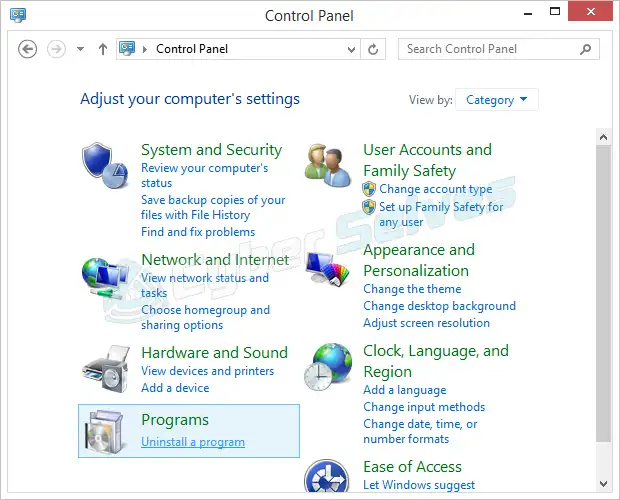
Step 2: To make the system of finding the threats more efficient, sort the list of programs by date so that the most recent entries are listed at the highest. Check the Name column for any entries that are unknown to you.
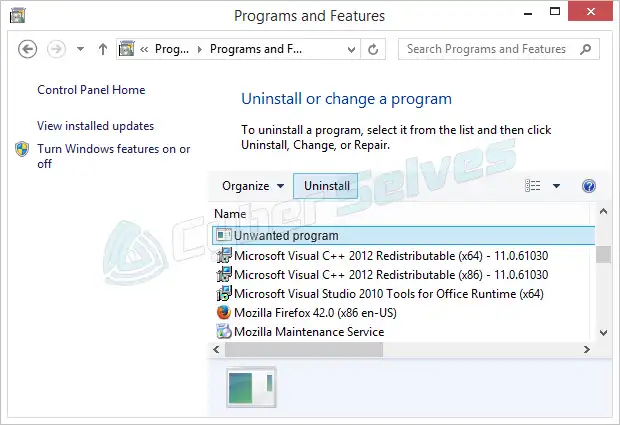
Step 3: Finally, after locating the potentially unwanted software, select “Uninstall” from the menu.
Conclusion
If you suspect sync-eu.exe.bid virus has made its way into your computer, you should act immediately to have it removed. Your chances of preventing the extensive and irreversible system to fail or files improve the sooner you eliminate the threat. If you suspect a Trojan is lurking on your pc, you can protect your computer including your data by following the steps outlined in the tutorial below.

![[2 Fixes] Avast Can’t Remove Virus](https://cyberselves.org/wp-content/uploads/2023/02/Avast-Cant-Remove-Virus.webp)